Paul Arveson
Nov. 10, 2000
Technology architectures consist of all the kinds of technologies (including software, hardware and services) that enable and support the creation, management and sharing of information in a business environment. Because of the rapid pace of technological change, it is difficult to even list the categories of these technologies. But even more than that, what we would like to have is a visual map that will illustrate the relationships between the categories of technologies, as they function in an organization. That is the task undertaken here.
The goals are to provide a map with the following features:
With these goals in mind, a new definition of the technology architecture categories was developed. This framework succeeds in meeting the basic goals, although it is not an "industry standard". Unfortunately, an appropriate "standard" framework for technology architecture does not appear to exist (there are numerous generic architecture descriptions, but none of them met our requirements for simplicity and fit to the organizational environment). It is nevertheless hoped that this framework will be stable enough to last for a few years.
Please note that the technology architecture is intended to provide a list of kinds of technologies used, or that may be used in the organization. It is not a map of the architecture itself, except in a very general way. It is not a map of the architecture of any system or product, e.g. it is not intended to represent a system with 3-tier architecture. Nor is it a "framework" in the Zachman sense. It is simply intended to serve as a list of technologies, organized into generic categories based on their actual relationships as used in SC.
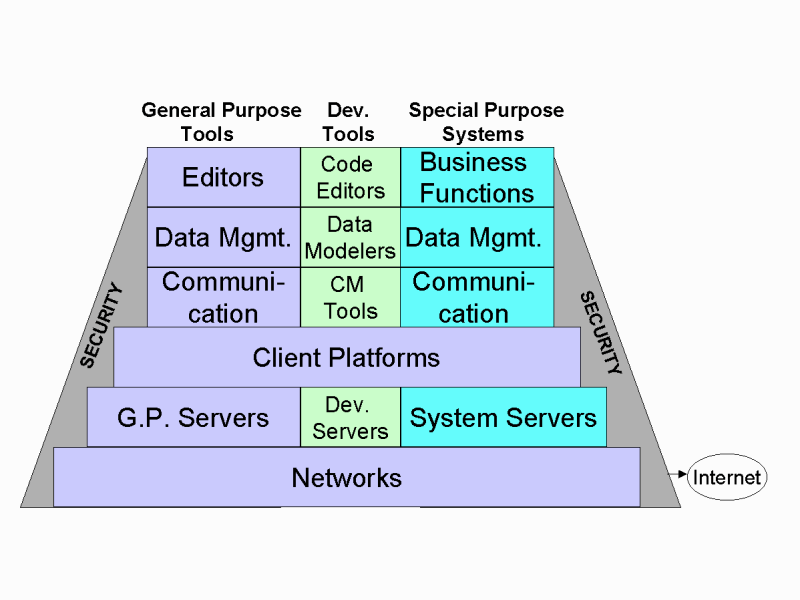
The following map illustrates the proposed new framework for technology architecture:

This architecture model is user-centric: three user-based categories of technologies were defined, corresponding to general purpose, developer, and special systems users, each of whom require a somewhat different set of technologies. These are represented by the three columns of the map in different colors.
This feature of the technology architecture was driven by the actual categories of IT usage in the Office. A major portion of our technology architecture is for the general purpose use of hundreds of people, and it is a standardized architecture. On the other hand, the special purpose systems are much more complex and require much more technology services; they have features quite different from the standard tools; they are not standardized; and they may have a limited number of specially-trained users. Therefore we distinguish between 'tools', which are software products for individual use, versus more complex and specialized 'systems', which support functions for a group or the enterprise as a whole. 'Services' refers to combinations of hardware, software, and operators. Finally, one set of special users is the developers, who require a specialized set of tools.
The map is divided into six technology layers. The top three layers identify the tools that help users to do their work. In general terms, users do three things with information technology:
1. Edit, create, author, modify, and manipulate documents in files.
2. Create, retrieve, update, store, delete and manipulate data in databases.
3. Communicate, share, store, retrieve and respond to information distributed among people.
(There are many more things that particular users may do, such as mathematical computation, but these are treated as special cases rather than enterprise architecture issues, so they are not considered here).
The lower three layers are 'utilities': services that are not directly provided to or from end users. Rather, they are services that support and maintain the services to and from end users. Hence all hardware items are considered utilities, i.e. appliances. For example, the Client Utilities layer includes all desktop computer hardware and software used to enable the top three layers to function on a desktop. In SC, most users use the same desktop software image running on a standard desktop computer. This fact is represented by the common platform under all the user software services.
Security services (represented by the sloping 'bunkers' on each side of the picture) are pervasive. Every category has security requirements and technologies appropriate to that category. Since these technologies differ depending on the category, it was thought appropriate to include security technologies over the whole picture, with the stipulation that security will be included within each category.
A consistent user-centric viewpoint helps viewers to quickly orient themselves and find the topics they are looking for. That is how this model avoids the confusion seen in architectures that use ambiguous terms such as "services" and "platforms" which are used in many different ways; and the use of terms such as "enterprise" and "infrastructure" which are nebulous and not user-centric.
The Servers layer includes all hardware and software associated with centralized services. Those in the General Purpose column include login, email, web, directory and Internet access services that support all users. Developers have their own special servers for new software development, testing, configuration management, etc. Business systems will have their own servers to support special requirements.
Underlying all services is the Network layer, which (in SC) uses the same technologies across the organization and serves all applications.
Here then is an outline of the detailed contents of the technology architecture categories:
1. General Purpose Software Tools and Utilities
This category covers the desktop hardware and general-purpose software that is distributed via an image to all end user desktops, and most Notebook computers. These technologies provide the functionality to support the most common needs of the workforce. "General purpose" implies COTS products that do not require significant effort to implement.
1.1 General Purpose File Editing Tools
1.1.1 Document Editors
1.1.2 Spreadsheets
1.1.3 Project Management Tools
1.1.4 Graphics Editors
1.1.5 Speech Recognition Tools
1.1.6 Office Editing Suites
1.1.7 General Purpose File Utilities
1.1.8 File and Document Security Technologies (digital signatures, file vaults, watermarks,
anti-virus clients, etc.)
1.2 General Purpose Data Storage and Manipulation Tools
1.2.1 Shared File Systems
1.2.2 Personal and Workgroup Databases
1.2.3 Data Modeling Tools
1.2.4 Document Management Systems
1.2.5 Database Security Technologies
1.3 General Purpose Communication Technologies
1.3.1 Email (Messaging) Systems
1.3.1.1 Email Gateways and Interfaces
1.3.1.2 Email Utilities
1.3.1.3 Text-based Conferencing Systems, Chat Systems
1.3.2 Calendars & Scheduling Tools
1.3.3 Web (HTTP-based) Communications
1.3.4 Remote Access client/server Communications
1.3.5 Voice over IP, Audio Teleconferencing
1.3.6 Video Teleconferencing
1.3.7 Streaming Media Clients and Servers
1.3.8 Groupware, Collaboration Tools
1.3.9 Wireless Communications
1.3.10 Terminal Emulators
1.3.11 Help Desk and Call Management Systems
1.3.12 Reserved for future use
1.3.13 Communications Security Technologies (data encryption, key management, etc.)
1.4. General Purpose Client Platforms
1.4.1 Desktop Client Platforms
1.4.1.1 Desktop Computer Hardware and Interconnections
1.4.1.2 Desktop Computer Operating Systems
1.4.1.3 Remote Access Clients for Desktop Platforms
1.4.1.4 Local and Network Printers, Scanners, Cameras, and other Peripherals
1.4.1.5 Antivirus Software for Desktop Clients
1.4.1.6 Removable Storage Media for Desktops
1.4.1.7 Backup and Restore Systems
1.4.1.8 Desktop Security Technologies - smart cards, authentication, identification, expiration,
physical security
1.4.2 Notebook Client Platforms
1.4.2.1 Notebook Computer Hardware and Interconnections
1.4.2.2 Notebook Computer Operating Systems
1.4.2.3 Remote Access Clients for Notebook Platforms
1.4.2.4 Portable Printers, Scanners, Wireless, other Peripherals (including
PCMCIA cards)
1.4.2.5 Antivirus Software for Notebook Clients
1.4.2.6 Removable Storage Media for Notebooks
1.4.2.7 Backup and Restore Systems
1.4.2.8 Notebook Security Technologies - smart cards, authentication, identification, expiration,
physical security
1.4.3 Hand-held and Wearable Client Platforms
1.4.3.1 Hand-held and Wearable Computer Hardware and Interconnections
1.4.3.2 Hand-held Computer Operating Systems
1.4.3.3 Remote Access Clients for Hand-held Platforms
1.4.3.4 Portable Hand-held and Wearable Computer Peripherals
1.4.3.5 Antivirus Software for Hand-held Platforms
1.4.3.6 Removable Storage Media for Hand-held Platforms
1.4.3.7 Backup and Restore Systems
1.4.3.8 Hand-held Device Security Technologies - authentication, identification, expiration,
physical security
1.5 General Purpose Server Hardware and Software
1.5.1 Application Servers (COTS)
1.5.2 Database and File Servers
1.5.3 Directory Servers
1.5.4 Internet Servers (outside firewall)
1.5.5 System Management Servers, Server Administration Utilities
1.5.6 Hardware - server computers, disk drives, interconnections
1.5.7 Removable Storage Media for Servers
1.5.8 Backup and Restore Systems and Utilities
1.5.9 Application-layer Security Servers (login servers, proxy servers,
certificate servers, antivirus filters, alert systems, etc.)
1.6 Networks
1.6.1 Network Operating Systems
1.6.2 Transmission Protocols and Technologies
1.6.3 Packet Switching Hardware - hubs, switches, routers
1.6.4 Cable Hardware - copper cables, fiber optics, interconnections
1.6.5 Wireless Network Hardware
1.6.6 Network Administration Tools
1.6.7 Network-layer and Physical-layer Security Technologies - (firewalls, monitors, physical security)
2. Development Tools and Technologies
This category includes a wide range of special tools (CASE tools) to support the work of software and system development. Although there are many other business processes within the organization, this work is special enough to require its own category of technologies.
2.1 Development Editing Tools
2.1.1 Programming Languages
2.1.2 Integrated Development Environments and other Code Editors
2.1.3 Graphical Tools and User Interface Editors
2.1.4 Document Conversion Tools
2.1.5 Code Validation and Testing tools
2.1.6 Data Modeling Tools
2.1.7 Application Design Tools
2.1.8 Code Security and Access Control Utilities
2.2 Development Databases and Utilities
2.2.1 Document and Code Repositories
2.2.2 Enterprise Resource Management Systems
2.2.3 Database Security Access Control Utilities
2.3 Development Communication Tools
2.3.1 Configuration Management and Version Control Tools
2.3.2 Software Project Management and Monitoring Tools
2.3.3 Developer Access Control Utilities
2.4 Development Servers
2.4.1 Testing and Evaluation Software
2.4.2 Special Hardware (e.g. testbeds, laboratory equipment)
2.4.3 Security Utilities for Development Environments
3. Special Purpose Business Systems and Utilities
This category includes the complex, often custom-built systems that perform special business
functions and for which technologies have been defined. It also
includes prescribed or recommended technologies to be used in the engineering of
new systems. This category covers major "enterprise-level" software tools and services which are not found in the general purpose
architecture. Security features are not included in these categories,
because they are covered in the general-purpose categories that
will be used by the business applications.
3.1 Business System Logic
3.1.1 Software Source Code and Scripts
3.1.2 Software Components
3.1.3 Distributed Component Systems
3.2 Data Management Technologies for Business Systems
3.2.1 File System Databases
3.2.2 Relational Database Systems
3.2.3 Object Database Systems
3.2.4 Management Information Systems
3.3 Communication Technologies for Business Systems
3.3.1 Portals
3.3.2 Workflow Systems
3.4 Business System Servers
3.4.1 Special Business Application Servers